In 2018 I wrote a quick post on how to flood phishing pages with a python script. Unfortunately that doesn’t work with python3 anymore and also doesn’t handle POST request, me not really being a python dev decided to use bash with two packages instead of coding something in ruby.
Install packages
apt install pwgen gpw
That’s it for the packages, now you have something to generate usernames and passwords.
Gather the fields
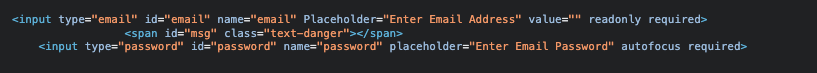
Looking at the page sources shows two fields being used, a field email and password.
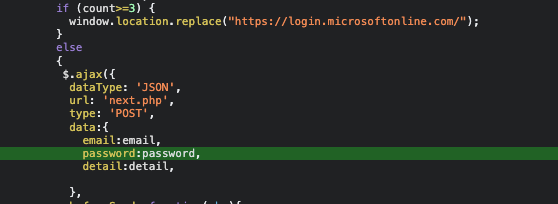
Now what happens once the user clicks on submit?
If the user has tried 3 times, a redirect to the real microsoft page will be triggered. The first requests however are passed on to a next.php via POST Request.
The Script
for ii in {1..500}
do
EMAIL=`gpw 1`@`gpw 1`.com
PW=`pwgen -s 10`
curl -X POST -F "email=$EMAIL" -F "password=$PW" https://some.phishing.url.com/next.php; echo "$ii posted $EMAIL/$PW"; done
nothing fancy but should be enough to fill up the phishing site with a lot of crap data.
Photo by Antoine GIRET on Unsplash